NEW SCAM ALERT!!!
ADWARE AND INTERNET SCAMS
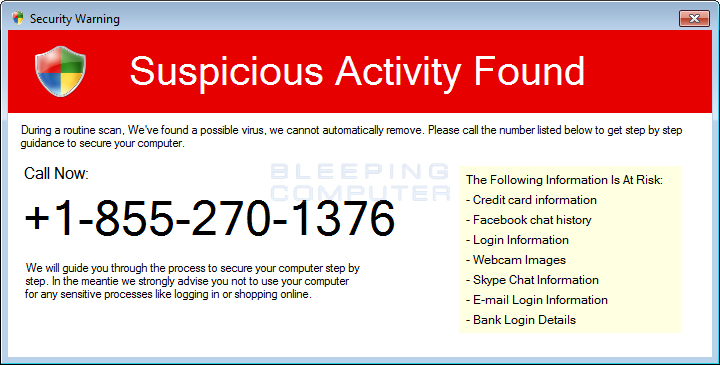
If you see a screen pop up ad that suggests that you call a number on your screen….
STOP-CALL US
Ask for Rod or Harley at 785-527-5626
Do not call any screen popups phone#. Even if they are an Okay Outfit or Business, you will give control of your computer to them and have to pay them with a credit card. They then have your name, phone number, credit card # and IP address. This is all that they need to hijack your identity.
If you are seeing pop-ups on your screen asking you to call a phone number to fix your computer, then your machine probably is infected with an adware or a potentially worse unwanted program. These pop-ups are caused by an ad-supported extension.
The malicious browser extension is typically added when software gets bundled into their installation program. When an adware extension is installed on your computer, it can be triggered to open whenever you open a new tab within the web browser, resulting in an ad to pop-up.
The pages are usually malicious websites which are used by cyber criminals to promote their remote support services. The bogus pop-up ad will state that your computer is infected and that you need to call their paid support service to remove the infection. This is a bogus claim, and an attempt to make you pay $100 to $400 for their malware removal “services.”
Other common symptoms include:
- Advertising banners are injected with the web pages that you are visiting.
- Random web page text is turned into hyperlinks.
- Browser popups appear which recommend fake updates or other software.
- Other unwanted adware programs might get installed without the user’s knowledge.
You should always pay attention when installing software because often, a software installer includes optional installs. Be very careful what you agree to install.
Always opt for the custom installation and deselect anything that is not familiar, especially optional software that you never wanted to download and install in the first place. You should not install software that you did not ask for.
![]() Security Alert – Petya Next-Generation Ransomware
Security Alert – Petya Next-Generation Ransomware![]()
The newest ransomware (malicious software that interferes with your computer’s functioning and requires a ransom to restore it) is even more problematic than previous types, because it not only prevents access to your documents — it locks you out of your computer entirely. This file, called Petya, is typically transmitted via email. If you open the attachment, or follow the link, it begins running on your computer.
Once this happens, you’ll see a series of things happening, including the Blue Screen of Death, the Windows Check Disk running, and a screen showing a skull and informing you of the ransom you have to pay to get your computer to function again. If you choose to pay the ransom, you’ll have to use another computer to do it.
Fortunately, you have a couple of other options to try. Take your computer to an IT technician, who may be able to recover your system. Or, if possible, shut down your computer immediately when you see the Blue Screen of Death. At this point, you may still be able to salvage your files.
Of course, the best strategy is to prevent the file from infecting your computer in the first place. To do this, use standard malware prevention techniques:
-
Be wary of all email you receive, especially from people you don’t know. Don’t open any attachments from an unknown source and don’t follow any links unless you know where they go.
-
Use complex, varied passwords and keep them private.
-
Only download software from known, trusted websites.
-
Keep your operating system, browser, and all applications up to date. Regularly install security patches and other updates.
-
Use an anti-virus and anti-malware application, and run it regularly to ensure continuous protection.
-
Perhaps most importantly, back up all your files regularly. Use a reliable offsite backup and recovery service..
While there is a lot of potential danger in computer and online use, there are also many steps you can take to protect yourself.
A NATIONWIDE SCAM TARGETING TAXPAYERS CONTINUES TO GROW.
In a new effort to take money from unsuspecting victims, fraudsters are sending out phony tax bills on what purports to be official IRS letterhead. They are also sending out e-mails from false websites that contain “IRS” in the Web address. In addition, scammers claiming to be IRS employees continue to call taxpayers, telling them they owe taxes and must pay up fast. Keep your guard up and don’t fall victim to any of these scams.
NEW SCAM ALERT!!!
 |
NEW SCAM ALERT!!!
 |
NEW VIRUS ALERT!!!
 |
|
Hacker Alert – Another Data Breach At A Big Retailer
How can this happen? Hackers scan merchants’ networks for ways to gain remote access, such as through outside contractors who have access to a computer network. Once they find that opening, they install malware that is undetectable by antivirus products. The Department of Homeland Security and the Secret Service estimates that more than 1,000 U.S. businesses have been infected with malware designed to siphon payment card details from cash registers in stores. Home Depot is offering free identity protection and credit-monitoring services to any customer who used a credit or debit card at any of its affected stores. Read more from Home Depot at this link. Retailers, banks, and card companies have responded to the breaches by speeding the adoption of microchips in U.S. credit and debit cards. That technology helps make transactions more secure. Home Depot says it plans to have chip-enabled checkout terminals at all of its U.S. stores by the end of this year. As a matter of routine, closely monitor your payment card accounts and report unusual activity to your issuing bank.
©2014 Cornerstone Publishing Group Inc. Trademarks: All brand names and product names used in this eNewsletter are trade names, service marks, trademarks or registered trademarks of their respective owners. |
 |
|
Malware Alert – Cyber Pandemic Known As GameOver Zeus
GameOver Zeus is capable of evading antivirus software. It monitors and injects rogue code into Web browsing sessions when users access banking and other popular websites from infected computers, and can infect a user’s machine when they open a PDF or click on a link sent to them in an email. Once set up on the computer, GameOver Zeus will intercept all financial transactions and rewrite them, so that payments made by the user will be redirected into other accounts. The malware also has the power to disguise unapproved payments that are made, meaning that thefts might have occurred even if accounts appear normal. Could your computer be infected with GameOver Zeus? Here are some warning signs:
If you notice one or more of these actions on your computer, you may have been infected with GameOver Zeus. The Department of Homeland Security’s Computer Emergency Readiness Team (CERT) has posted information on its website including an overview of the malware and actions you can take to
©2014 Cornerstone Publishing Group Inc. Trademarks: All brand names and product names used in this eNewsletter are trade names, service marks, trademarks or registered trademarks of their respective owners. |
![]() Social Media Alert – Watch Out For Social Media Spam (And Scams)
Social Media Alert – Watch Out For Social Media Spam (And Scams) ![]()
In the first half of 2013, spam — the scourge of the Internet since 1993 — grew by 355 percent across the Internet’s most popular social networks. This is according to data from Nexgate’s State of Social Media Spam Report. It shows that about 1 in 200 social messages contain spam. Facebook and YouTube were the most infected, containing more spam than other social networks by a ratio of 100 to 1. Facebook also has the largest number of phishing attacks — schemes in which a victim’s password or credit card information is hacked.
Social media spam is growing at high rates due to spammers moving away from email. Why? It’s harder to detect spam on social media sites and spammers can potentially reach millions of people with a single ad or post. Spammers have also developed a variety of ways to trick users with appealing visuals beyond the typical spam email.
What should you do? The Better Business Bureau recommends the following:
-
Never reveal overly personal or financial information on a social media site.
-
Avoid following unfamiliar or unknown links or pop-up ads.
-
Make sure to keep up with the latest operating systems, software, web browsers, antivirus protection and apps for the best defense against viruses, malware, and other online threats.
-
Report any possible spam to the appropriate people within the organization, including network administrators. They can be alert for any suspicious or unusual activity.
-
If you believe your financial accounts may be compromised, contact your financial institution immediately and close the account(s). Monitor all accounts for suspicious activity.
In addition, when browsing users’ profiles or pages, remember that not everything on these pages may be safe. Despite the circle of trust that social media sites create, cybercriminals are constantly lurking behind virtual corners, just waiting for opportunities to strike..
![]() Phishing Alert – Watch For Fraudulent Package Delivery Emails
Phishing Alert – Watch For Fraudulent Package Delivery Emails ![]()
Scammers take every opportunity to trick you into doing what they want and the holidays are no exception. Here’s how their holiday package delivery con typically works: They send you an email (claiming to be from FedEx, UPS, etc.) that describes a missed delivery or shipping address problem and tells you to click on a link to correct the issue. The link goes to a spoofed website which attempts to gather critical information like passwords, Social Security numbers, credit card numbers, and more. Don’t be fooled. The FedEx website says, “FedEx does not request, via unsolicited mail or email, payment or personal information in return for goods in transit or in FedEx custody.” The same is true for the other major package delivery services.
Another similar trick is an email supposedly from the U.S. Postal Service regarding an intercepted package delivery. The email contains a link that, when activated, installs a virus that steals personal information on your computer. Sometimes these emails elicit a sense of false urgency by stating that if you do nothing, you will be charged money.
The best way to combat this type of scam is to avoid opening suspicious, unsolicited emails or clicking on links within them. Warning signs of bogus emails include:
-
Unexpected requests for money
-
Requests for personal information
-
Links to familiar-looking websites that are actually spelled wrong
-
Extensive spelling and grammar errors in the body of the email
You can also adjust the settings in your email application to capture more spam in a junk folder. When you do see emails like these in your inbox, delete them immediately.
 Scam Alert – Ransomware Senders Demand Money to “Fix” Files
Scam Alert – Ransomware Senders Demand Money to “Fix” Files 
One of the latest ways for cybercriminals to try and get money from you involves infecting your computer with a virus that encrypts your valuable files (making these files unusable) then demanding a payment to decrypt them. This type of virus, called ransomware, can be installed on your computer if you open an attachment from a malicious sender.
A recent version of ransomware, called CryptoLocker, is often distributed via email messages that appear to come from reputable organizations or companies such as the Better Business Bureau, FedEx, and UPS. CryptoLocker can also be installed along with infected downloaded software.
Security experts warn to NEVER PAY THE RANSOM; you’ll lose your money and probably get nothing in return. If you do fall prey to ransomware, a number of legitimate security vendors offer solutions for unlocking machines. Talk to a local computer technician you trust for more information.
Of course, the best solution is to not become a victim of ransomware in the first place. Be extremely wary of email attachments, even if they appear to be sent by someone you know. (Viruses are often sent via one person’s email to others on their contact list.) Be particularly cautious about attachments other than typical office documents, especially ZIP or EXE files. Finally, be sure to have up-to-date commercial antivirus software active at all times.
Important! Please Read below!
Local businesses have been receiving phone calls from an organization asking for sponsorships to publish a directory of emergency numbers. The callers are claiming to need sponsors on behalf of the Belleville Public Library. This directory is NOT sponsored by the library and we urge you NOT to participate!
 Facebook Alert – Beware of Six Flags Season Tickets Giveaway
Facebook Alert – Beware of Six Flags Season Tickets Giveaway 
You may have seen Facebook posts recently that claim Six Flags theme parks are giving away free season tickets to those who “Like” and “Share” a promotional image and click on a link to claim their prize. These claims are false. The promotion has no connection to Six Flags whatsoever and the theme parks are not giving away free season tickets. Instead, it’s an attempt by online scammers to get people to “Like” and “Share” bogus promotional material and participate in survey scams.
By posing as a well-known entity and offering attractive prizes as bait, the “Like Farmers” running the scheme hope to amass a large number of “Likes” for their fake Facebook Page in a short period of time. Pages with large numbers of “Likes” can later be sold on the black market to other scammers and unscrupulous Internet marketers. The pages can then be re-purposed and used to promote dubious products and services to a wide audience or to launch other scam campaigns. They may also be used to trick users into divulging personal information by informing them that they’ve won a (non-existent) prize. Be wary of any Facebook post or page that promises expensive prizes in exchange for simply clicking on “Like” or “Share” and don’t take action when you see them.
Go here to read the response from Six Flags to this questionable program that’s using their name.
 Scam Alert – Phishing Emails That Appear To Be From Major Banks
Scam Alert – Phishing Emails That Appear To Be From Major Banks 
Phishing emails purporting to be from major national banks such as Wells Fargo and Bank of America are on the rise, so please be extra vigilant when going through your inbox. These fraudulent emails may look remarkably like ones from your bank and contain alerts about frozen accounts or unusual activity – messages created to frighten you into clicking on a link in the email to correct the issue. Users who did click on such links have had money stolen from their bank accounts.
Don’t fall victim to these phishing scams. It’s safest to never click on a link in an email that claims to be from your bank. If you get a message that looks even vaguely real, it’s much better to open a browser window and type in the URL of your bank’s home page and log in as normal.
 Scam Alert – Fake Antivirus Phone Scam Is Stealing Money And Identities
Scam Alert – Fake Antivirus Phone Scam Is Stealing Money And Identities 
Many online scams start with an email but you also need to be cautious when the phone rings. There have been an increased number of reports recently of phone scammers claiming to be from Microsoft, or an antivirus company, or some random tech support facility. These callers will claim their systems have detected viruses and/or malware on your computer and they can help you with a lifetime of guaranteed support for just a one-time payment of $100 or so.
The process typically goes like this:
-
The scammers first want you to download a remote access service and grant them access to your PC.
-
Next the scammers want you to buy and install antivirus software that’s usually counterfeit or just a trial version that leaves you with non-functioning, useless protection. They may also recommend the latest Windows operating system, which is also likely to be counterfeit.
-
Because the scammers were given unfettered access to your PC through the remote access service, they may install a backdoor Trojan — a malicious application that enables them to steal your passwords, use your system and Internet connection to send spam, and more.
If you receive a call from someone saying your PC has been compromised, just hang up the phone. Reputable companies will not make unsolicited calls about the health of your computer.
Microsoft recommends these do’s and don’ts to help prevent becoming a victim:
DO
-
Be suspicious of unsolicited calls related to a security problem, even if the caller claims to represent a respected company.
-
Use up-to-date versions of operating system and application software.
-
Make sure security updates are installed regularly.
-
Use strong passwords and change them regularly.
-
Make sure your firewall is turned on and that antivirus software is installed and up to date.
DON’T
-
Provide personal information, such as credit card or bank details, to an unsolicited caller.
-
Go to a website, type anything into a computer, install software, or follow any other instruction from someone who calls out of the blue.
-